How To Protect Your Company Against Fraud
Steadily increasing risks of fraud
Fraud is a growing phenomenon. In recent years, it has increased significantly not only against individuals but also against businesses. In fact, according to a report by Ardent Partners nearly 40% of businesses experienced an attempted fraud in the past year.
Companies, however, rarely want to admit they have fallen victim to an attack, so business fraud is not highlighted.
Get Controls in Place
While it is often assumed the criminals committing fraud are external to the organization, employees can also be found to be responsible. It shouldn’t be that surprising, since they would understand the company’s systems best.
Take the example of Swedish municipality, Katrineholm, that was left exposed when an employee was able to exchange the supplier account number for their own, as there was no four eyes policy in place. (The four eyes principle, also known as the two-person rule, stipulates that two individuals must approve an action before it can be taken.)
The payment was seemingly made to the correct supplier, but in reality it had been paid to the employee and the company was faced with the reality of losing 257,000 Swedish Krona (nearly $25,000 USD). In this instance, the municipality was able to trace who was responsible and retrieve their money but it could easily have been a different story. Another case that has been highlighted in media saw a department head of a large technology company approve false invoices of just over 5,6 million SEK ($425,000 USD) made out by an accomplice at another company at which they were both part owners.
So, how safe is your Accounts Payable? How proactive is your finance team? What actions should you be focusing on? We’re going to cover the six steps you need to take now to protect your company against fraud.
1. Identify the gaps
It is important to examine all the steps in your payment process. Think about the potential risk points from when the invoice first arrives, through the data capture and approval stages, right through to it entering your ERP system and the final payment file transfer/settlement.
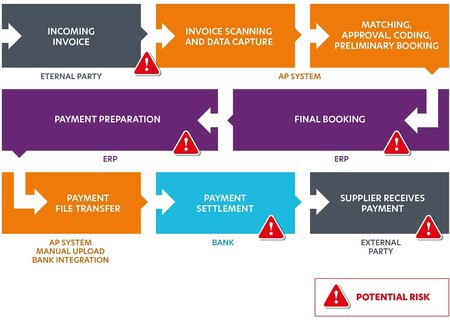
Invoice receipt is one obvious point where you are vulnerable whether you have system support or not. Fraudsters are using increasingly sophisticated methods to hack into the email system of your suppliers and create invoices that appear to be from a legitimate email address. Even Google and Facebook were duped into transferring $100m into a Lithuanian man’s account when he pretended to represent a Taiwanese hardware firm and submitted fake invoices.
If the suspect invoice is not spotted at this point it can be difficult to catch at a later stage which is why it is vital to have either manual or automated controls in place. An automated system will set various parameters and its interpretation engine will flag up anomalies against the usual transaction history.
The ERP bank file upload during payment is another particularly vulnerable point as it is the last step before the money leaves the account. Someone either internally or externally (should they be able to gain access to an employee’s email via phishing) could access the file before it has had time to be uploaded to the bank, change the account number and get it approved without anyone noticing. Yet, checking all the information and account numbers manually to prevent such attacks can be extremely time consuming.
2. Spotting Unusual Activity
You may expect to receive a certain number of invoices from a supplier each month. For other suppliers, you might have expectations for invoices of a certain dollar amount. So, if a supplier suddenly issues four times the number of invoices they normally would or the invoices are for unusually large amounts, alarm bells should start ringing. Automation is critical for flagging up such unusual patterns in the AP process. It captures every detail and is not susceptible to human error so will highlight duplicate invoices, track vendor changes or flag any changes that look suspicious.
Want to make your organization absolutely fraud-proof? Watch this on-demand webinar to learn the latest tactics of fraudsters, and how technology has evolved to help companies successfully protect themselves going forward.
3. Segregation of duties
It is imperative that the same person cannot complete all the steps in the payment process. Make sure there are policies in places that mean more than one person is involved in registering an invoice, setting up an account, creating a payment proposal, or changing the master data. Only that way can you prevent ‘Tim’ or ‘Monica’ in Accounting setting themselves up as a fake supplier, approving the transaction and paying themselves millions of dollars.
4. Automating the approval process
Automating your AP delivers a high level of visibility and introduces more control into the approval process, reducing the risk of financial losses. It makes it much easier to match invoices with their corresponding purchase orders and receipts. This means a red-flag will be raised if an attempted payment has no invoice to match against it or there is no record of goods received.
5. Audit trail and visibility
Auditors want to see evidence of traceability through an audit trail. This could be considered a reactive measure because it relies on errors being found after the event. But, by ensuring everything is traceable, it creates visibility. This in turn acts as a deterrent as users know whatever they are doing is logged and traceable.
6. Make it easy to do it right
Procedures may sound great in theory but if they are not easy to follow, they may as well as not exist. Remember, people are busy, so you need to make your processes as simple as possible. Otherwise, security is going to be compromised in the name of efficiency and speed. If you utilize technology in the right way, security and efficiency are not mutually exclusive.

Next steps
Do you have an anti-fraud strategy in place? If not, start developing one as a matter of urgency. If you do, consider when it was developed and what it covers. Does it reflect the latest technology available? Does it consider the new types of threats? If the answer is no or you’re not sure, you should explore how AI and automation can plug any gaps in your process from an invoice entering your system to it being paid.
Only by making the points on the invoice through payment journey as secure as possible and reviewing your process from a risk perspective from time to time, can you be confident your company will be protected.
Discover how to overcome four common financial hurdles and take control of your financial future.
We asked 2750 finance professionals about their most common financial hurdles. Have a look at the results and see if you can relate to what we discovered.







